iOS Application Security Part 35 – Auditing iOS Applications With iDB
In this article, we will look at another cool utility named iDB for pentesting iOS applications.
Before that, i would like to apologize for coming up late with this article. A lot of you have been requesting articles on different topics and i promise that i will write on them soon :). So since we are best friends again, let’s dive into this tool.
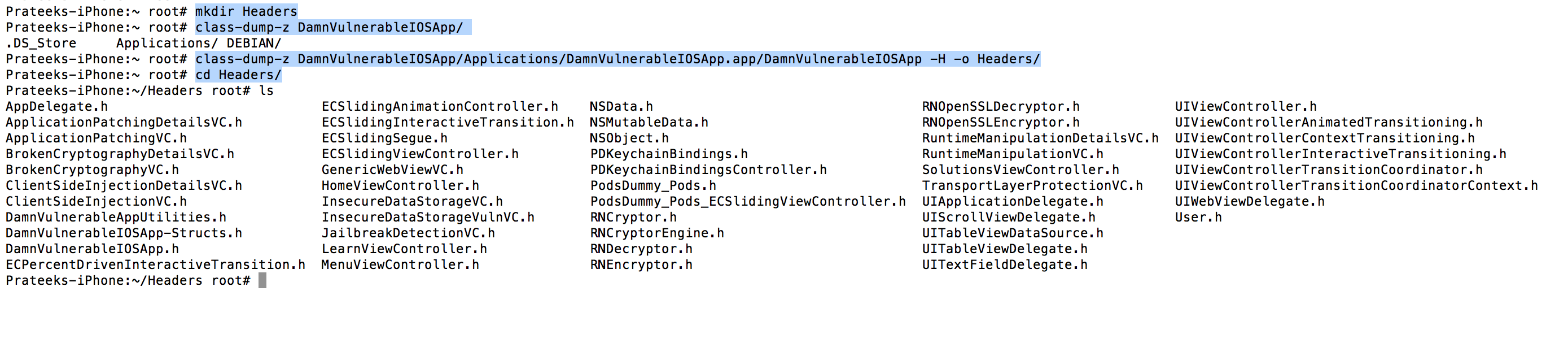
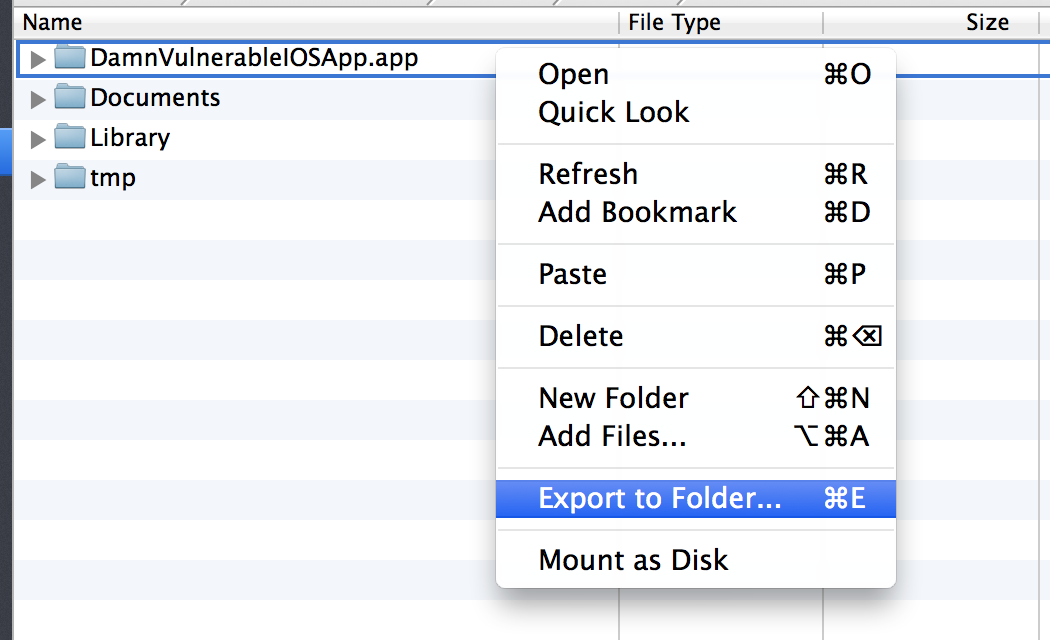
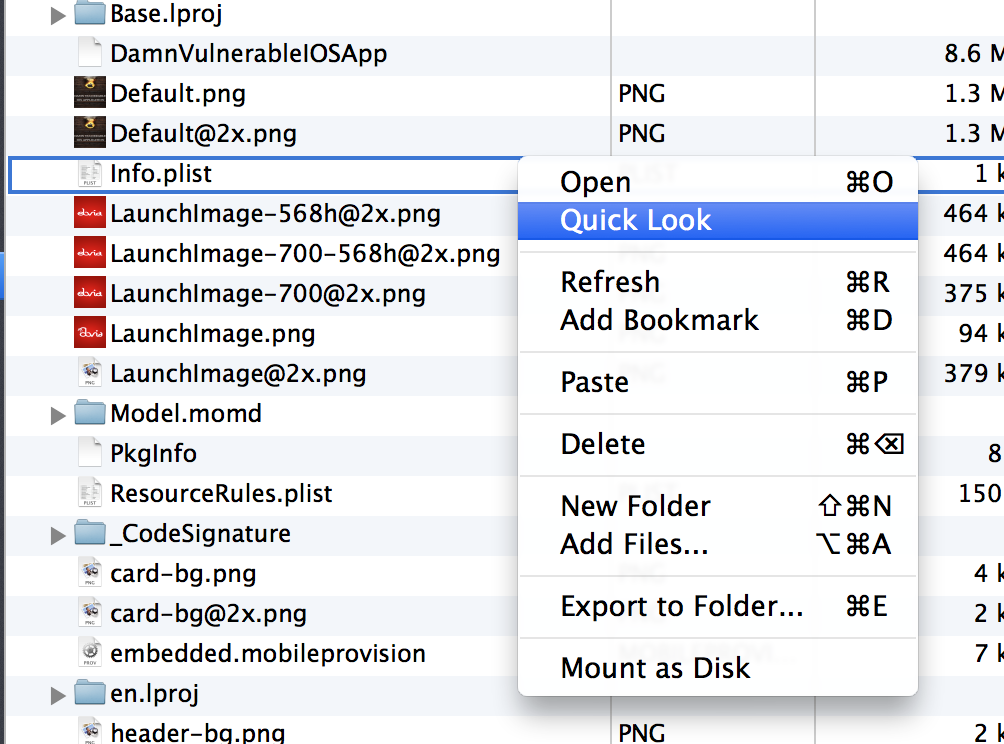
iDB is open source and you can download it from its Github page. You can then follow the tutorial here to know how to install it. Installation might take some time as there might be some dependencies you will have to install, so have some patience. Also, please note that it works with ruby versions 1.9 and 2.1 so make sure you set that version of ruby. You can use rvm list to list the versions of ruby installed on your system and then use rvm use followed by the version of ruby that you want to use.
Read on →